SSO Authentication with SAML
You can use the Security Assertion Markup Language (SAML) protocol to authenticate users in DRUID via single sign-on (SSO). DRUID supports any Identity Provider (IDP), including custom implementations. Once SAML is configured, users can sign in through a secure link displayed in their chat session.
How Does SAML Work?
The SAML protocol allows secure exchange of authentication information between your identity provider and DRUID. Here’s a simplified flow:
- A user clicks a login link in the DRUID chat.
- DRUID redirects the user to your IDP's authentication endpoint.
- The IDP authenticates the user and generates a SAML response.
- The response is returned to DRUID and processed.
- If the authentication is successful, the user continues in the conversation as an authenticated user.
DRUID holds the authentication session per conversation ID.
Configure the SAML SSO App
To use SAML authentication in DRUID, first create and configure a SAML app.
Step 1. Create a SAML App
To create a new OAuth2 app:
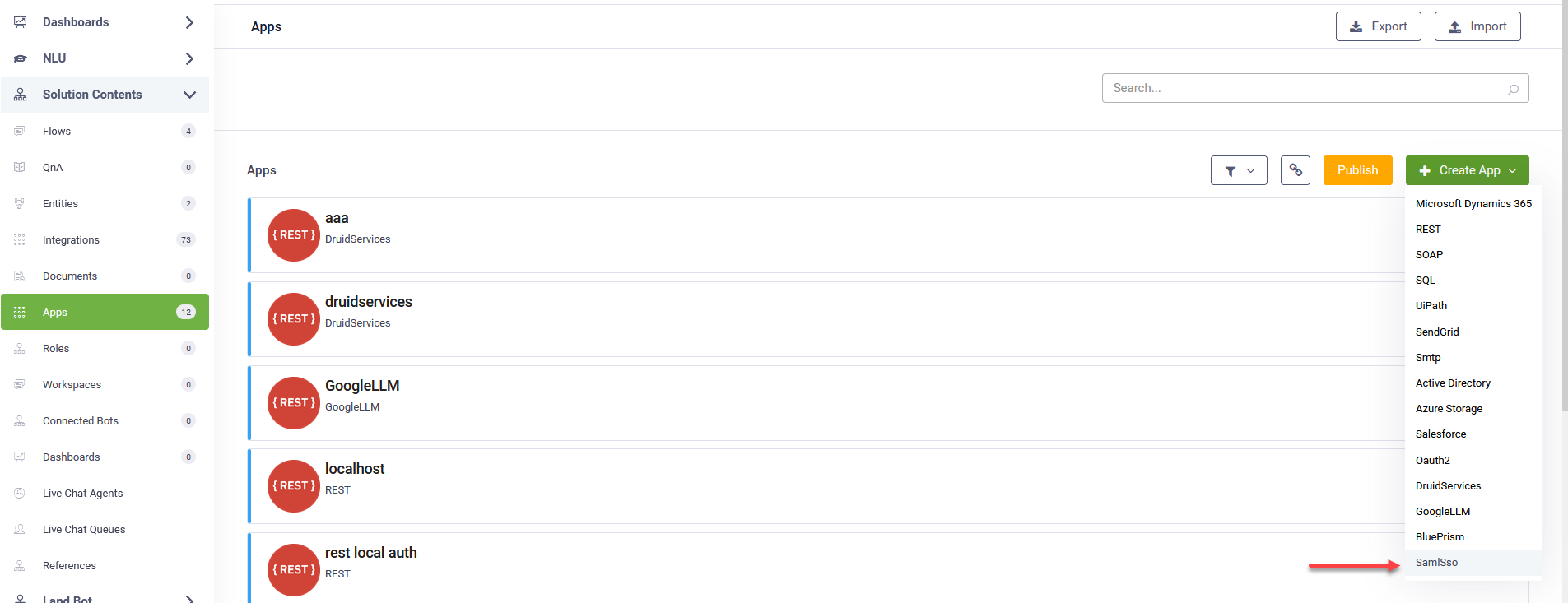
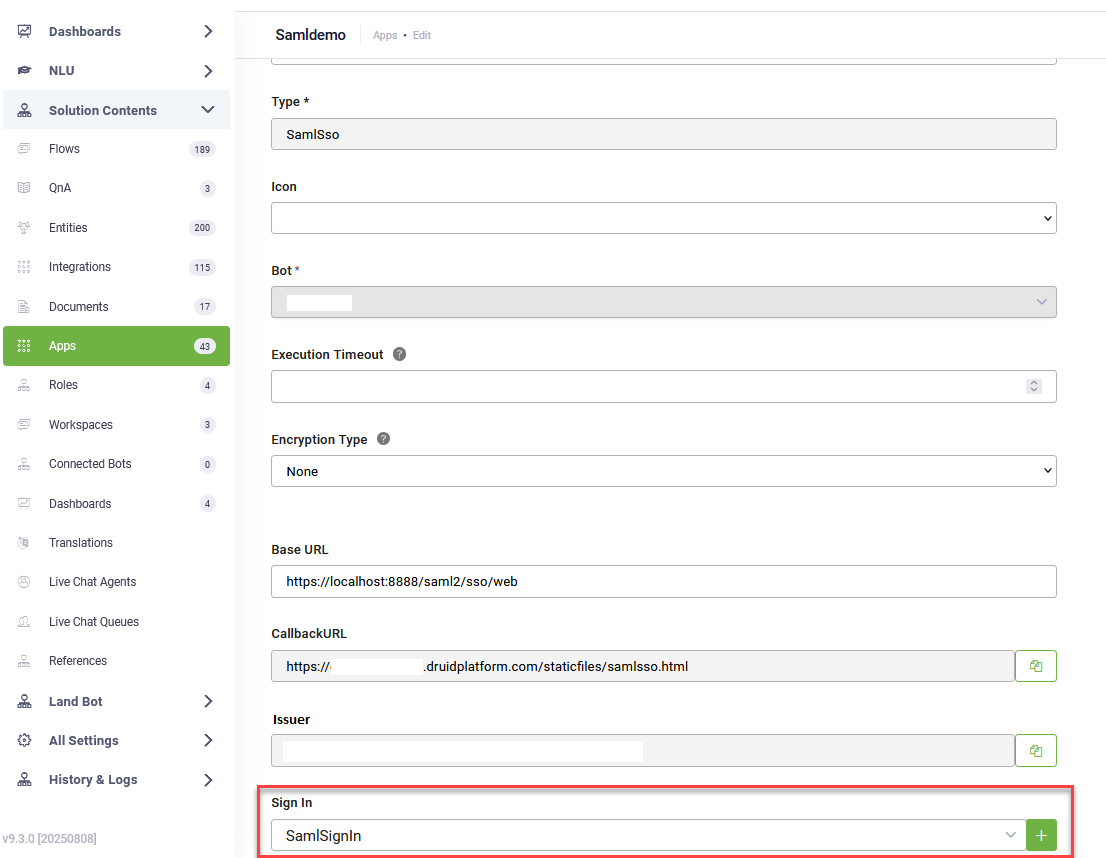
- In the DRUID Portal, go to Solution Contents > Apps.
- Click Create App and select SamlSso.
- On the New app page, configure the following parameters:
- Encryption Key – click the Generate button to generate the key, which will be used by the Encrypt Data task to encrypt the data and by the client / 3rd party application to decrypt the data and use it further.
- Secure encryption with salt – adds a random 64-bits salt to the data before encrypting it. Please note that using this feature requires the client to develop code for data decryption.
- Save the SAML app.
- Copy the Callback URL and Issuer and make sure your IdP can access them.
|
Parameter |
Description |
Mandatory |
|---|---|---|
|
Code |
Unique name to identify the app. |
Yes |
|
Execution Time |
The maximum number of seconds a request is allowed to execute. By default, the timeout for all connector integrations is 60 seconds. This setting will apply to all connector tasks that use this app. |
No |
|
Encryption Type |
Enables data encryption on the connector using the AES CGM encryption algorithm and allows bot authors to encrypt specific data before sending it to external REST apps, by using the Encrypt Data integration task as first task in the desired connector action. When you select AES CGM encryption algorithm (the only one currently available), two new options are available: For more information, see Encrypt Data. |
No |
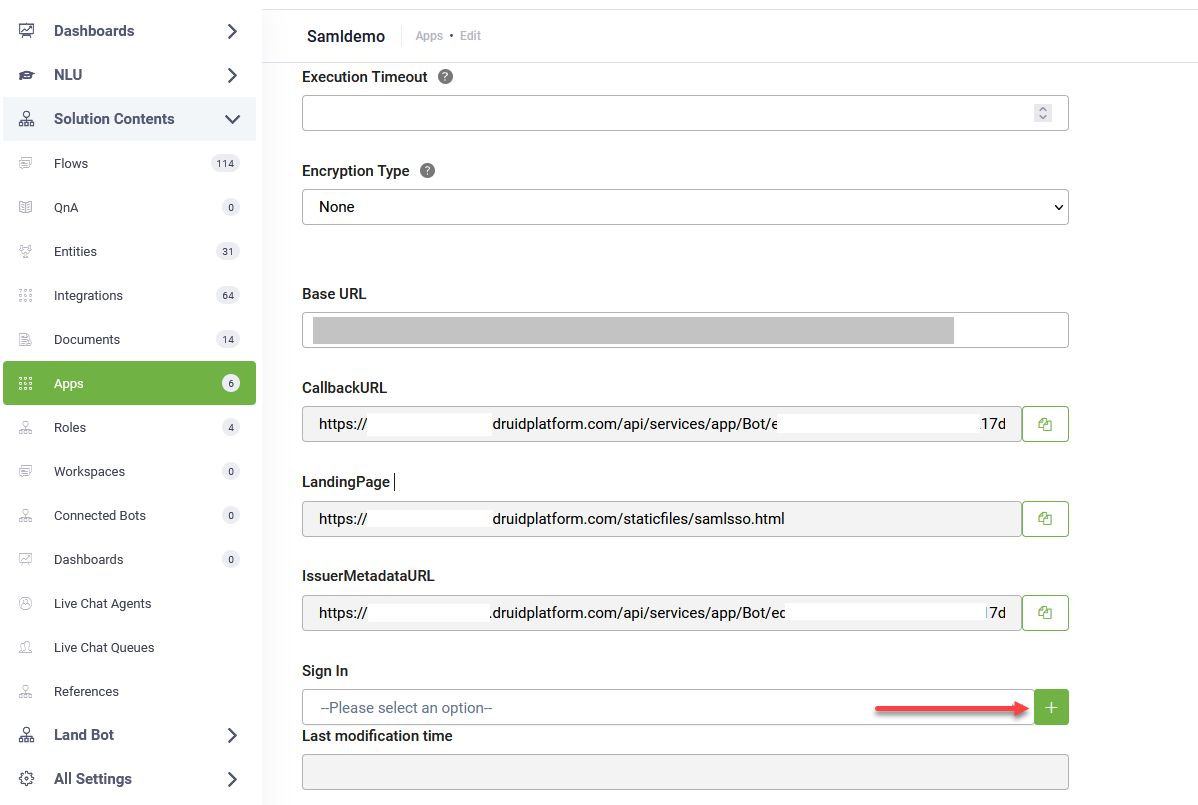
| Base URL | The metadata URL provided by your IdP. | Yes |
| Callback URL | The URL where DRUID expects the response from the IdP. The field is non-editable. | Yes |
| Landing Page | The DRUID-hosted login and consent page. At runtime, when a user clicks the login link in the chat, DRUID redirects them to this page. The field is non-editable. | Yes |
| Issuer Metadata URL |
The URL that the Identity Provider (IdP) uses to verify SAML AuthnRequests sent by DRUID when requests are signed with DRUID’s certificate. The field is non-editable. |
No |
Step 2. Define Sign In integration
The Sign-In action is required for user authentication. This integration processes the request and response data from the identity provider (IdP) and maps the required values back to Druid. For example, you can map the employee ID to use it for authentication.
To create a sign in with SAML integration, follow these steps:
- In the SAML app configuration page, click the add icon (
 ) next to the Sign In field.
) next to the Sign In field.
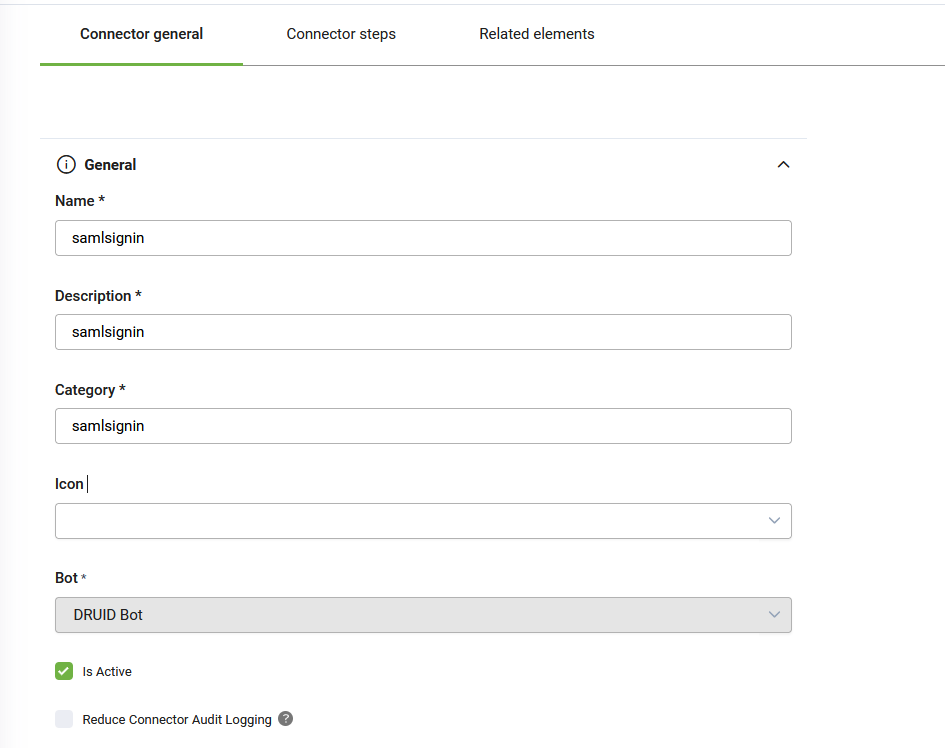
- Provide a Name, Description and Category and select Is Active.
- Click Save. The page refreshes and displays on the Connector steps tab.
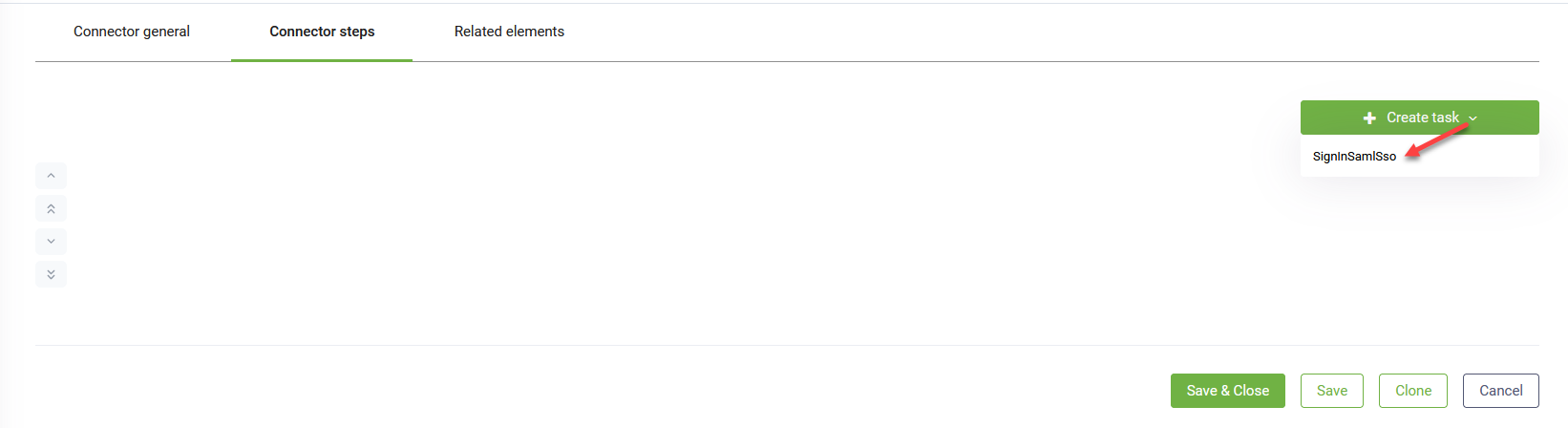
- At the top-right corner of the page, click the Create task button and select SignInSamlSso.
- Enter a Description and from the Connection Code drop-down, select the new SAML app app you created.
- Click on the Request tab. The integration Request is responsible for adjusting the SAMLRequest that DRUID sends to the IdP. By default, the request is generated, compressed, and URL-encoded, but not signed. If you have advanced XML knowledge, you can customize the XML in the request as needed.
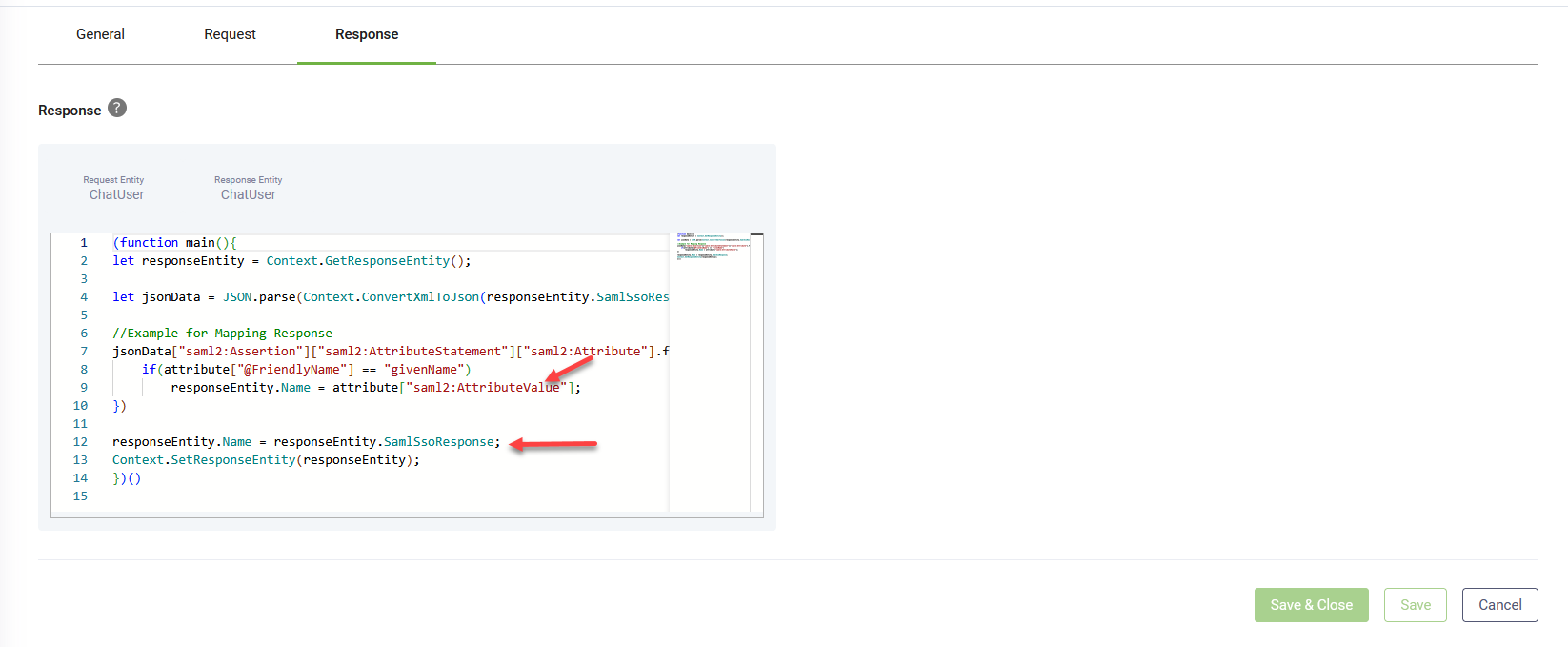
- Click on the Response tab. The integration Response is responsible for extracting metadata from the SAMLResponse received from the IdP and passing the required information to DRUID entities.
- Click Save & Close.
- Publish the integrations.
The Connector Action page appears on the Connector general tab.
The Edit Connector Action page appears on the General tab.
Sign SAML AuthnRequests
requestEntity.SamlSsoRequestUrl = App.SignSAMLRequest(requestEntity.SamlSsoRequestUrl, requestId);Map the XML response returned by your identity provider (IdP). DRUID provides a sample script to help you get started. Make sure you extract and assign all user attributes needed for your flow or system (for example, email, role, or username).
Step 3: Link the Sign In action to the SAML App
- Return to the SAML app configuration page.
- In the Sign In field, select the integration you created at Step 2.
- Click Save & Close.
- Publish the apps.
Signing in users with SAML
To prompt users to sign in using SAML:
- Go to the flow where you want to perform the authentication.
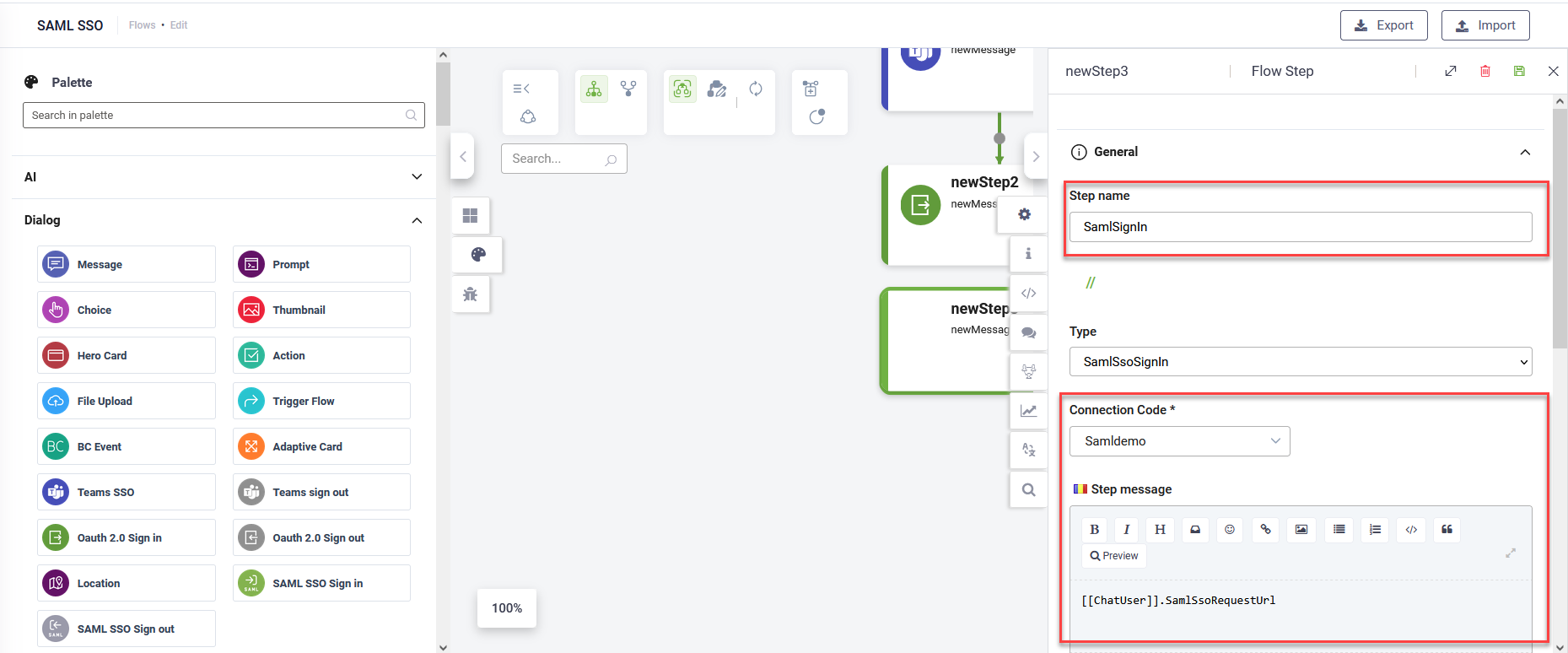
- From the Flow Palette, drag the SAML SSO Sign in step from the Dialog section.
- Drop it into your desired location within the flow.
- Configure the step as follows:
- Enter a step name.
- From the Connection Code drop-down, select the SAML connector app you created.
- In the Step message field, enter
[[ChatUser]].SamlSsoRequestUrl. - Save the step.
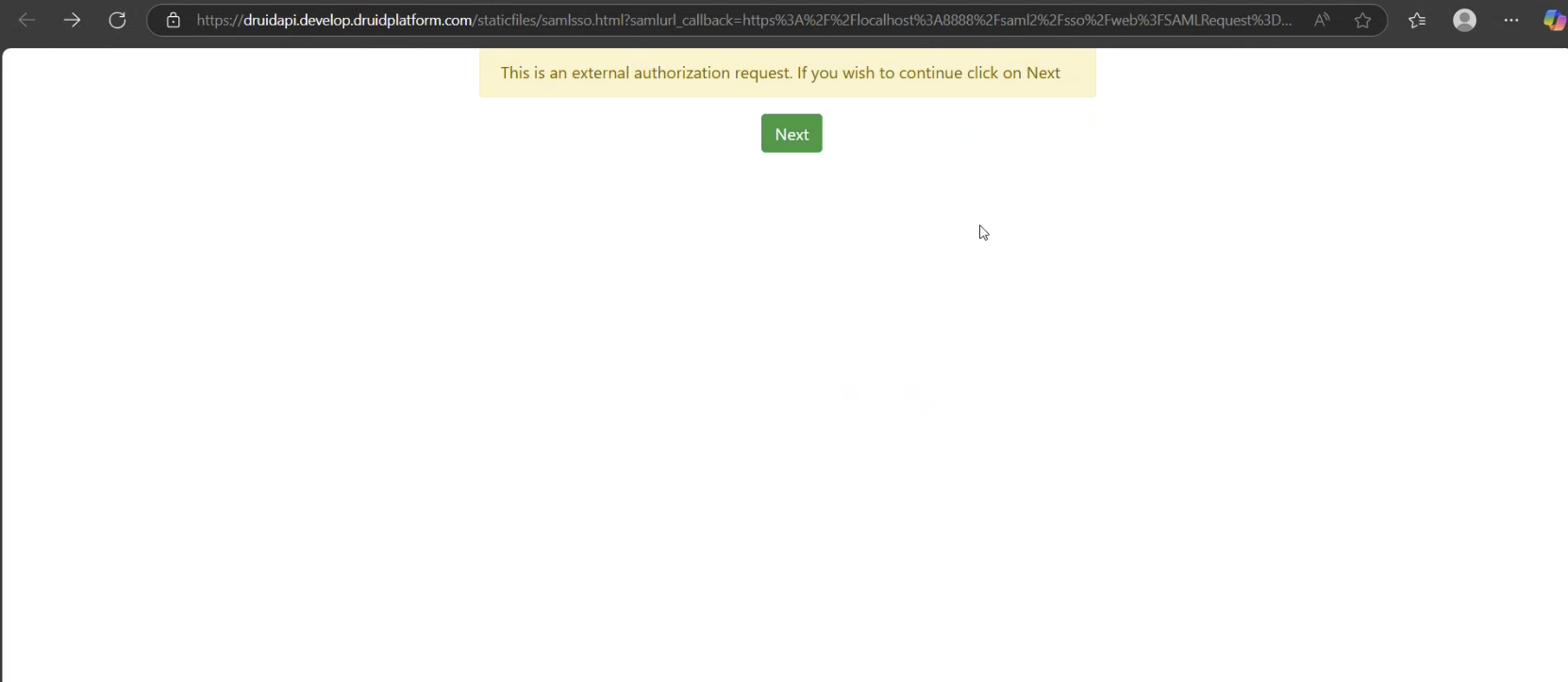
At runtime, when the user clicks the link in the chat, DRUID redirects them to a DRUID-hosted login/consent page at the WEB API service.
After the SAML SSO Sign In step, continue with DRUID-specific authentication using internal actions such as SaveIdentifiedUser and SaveAuthenticatedUser. You can configure these either in the next step of the flow or in the PostActions section of the SAML SSO Sign In step.
Signing out users authenticated with SAML SSO
There’s no special sign-out process for users authenticated with SAML SSO. To sign out a user, in your flow add a step that either uses the internal action SaveNotAuthenticatedUser or sets [[ChatUser]].IsAnonymous to true.